
In 2016, the European Parliament and Council established the first regulatory framework for cybersecurity in the European market. The “Security of networks and information systems” directive (known as the NIS directive, for Network and Information System Security) aims to ensure a uniform and reinforced level of protection of digital infrastructures.
1. What exactly did this directive, called NIS 1, consist of?
With the digital transformation of European societies and the increasing interconnection of Member States, the European market has become more vulnerable to cyber threats. It was therefore imperative to collectively ensure an appropriate level of security at the level of the European Union. With this in mind, in July 2016, the European Parliament and the Council of the EU adopted the Directive “Network and Information Security” (NAKED). Implemented at the national level as early as 2018, this directive aimed to strengthen the cybersecurity of the main players in ten strategic sectors, i.e. several hundred entities in France. Thanks to this device, these organizations were required to report their security incidents to ANSSI and to deploy protective measures in order to significantly limit the exposure of their critical systems to cyberattacks.
2. What changes does the adoption of the NIS 2 Directive bring?
The NIS 2 directive is distinguished by its major ambition. Built on the foundations of NIS 1, it marks a real evolution both at the national and European levels. Faced with increasingly sophisticated cyberattacks targeting a growing number of organizations that are insufficiently protected, NIS 2 reinforces its scope and objectives to offer increased security. The expansion of its scope is an unprecedented advance in the regulation of cybersecurity.

3. In what way is this directive a major strategic challenge in terms of cybersecurity for EU Member States?
In summary, the challenge is a harmonized strengthening of cybersecurity at the European level.
Securing information systems (IS) in Europe has become a necessity in the face of evolving threats and the increasing interconnection of Member States. Cyberattacks, whether criminal, state or opportunistic, are multiplying and gaining in sophistication, putting critical infrastructures such as energy, health or finance at risk.
The interdependence of economies and networks increases this risk: A security breach in one country can have a chain of consequences across the continent. To avoid these vulnerabilities, it is essential to harmonize cybersecurity standards. Without common regulation, each state would apply its own rules, creating disparities and loopholes that could be exploited by attackers.
Strengthening cybersecurity also aims to protect the sensitive data of citizens and businesses while strengthening Europe's digital sovereignty. This makes it possible to reduce dependence on extra-European technologies and to guarantee greater control over digital infrastructures.
Finally, the establishment of solid cybersecurity standards contributes to strengthening user trust and the resilience of digital services, a key factor for the competitiveness of European businesses.
4. Date of entry into force of NIS 2? Until when can we comply?
The NIS 2 directive, adopted by the European Union, aims to strengthen cybersecurity in the Member States. Each country had to transpose this directive into national law by 17 October 2024. However, in France, this process has been delayed.
Background of the delay in France:
- Dissolution of the National Assembly: On 9 June 2024, the National Assembly was dissolved following the results of the European elections. This political situation has interrupted the examination and the vote of the bill necessary to transpose the NIS 2 Directive.
- Legislative delay: As a result, France was unable to meet the 17 October 2024 deadline for transposing the directive.
- Formal notice by the European Commission: On November 28, 2024, the European Commission officially notified 23 Member States, including France, for their delay in transposing the NIS 2 Directive.
It is important to note that France is not the only country affected by this delay. By the deadline of 17 October 2024, only three of the 27 member states of the European Union — Belgium, Croatia and Hungary — had adopted the laws necessary to transpose the NIS 2 Directive into their national legislation.
This context highlights the challenges France faces in aligning its national legislation with European cybersecurity requirements. To date, no exact version is known for the French transposition. However, given the length of compliance projects, it is important for French companies to start these projects now.

5. Which entities are affected by the NIS 2 directive?
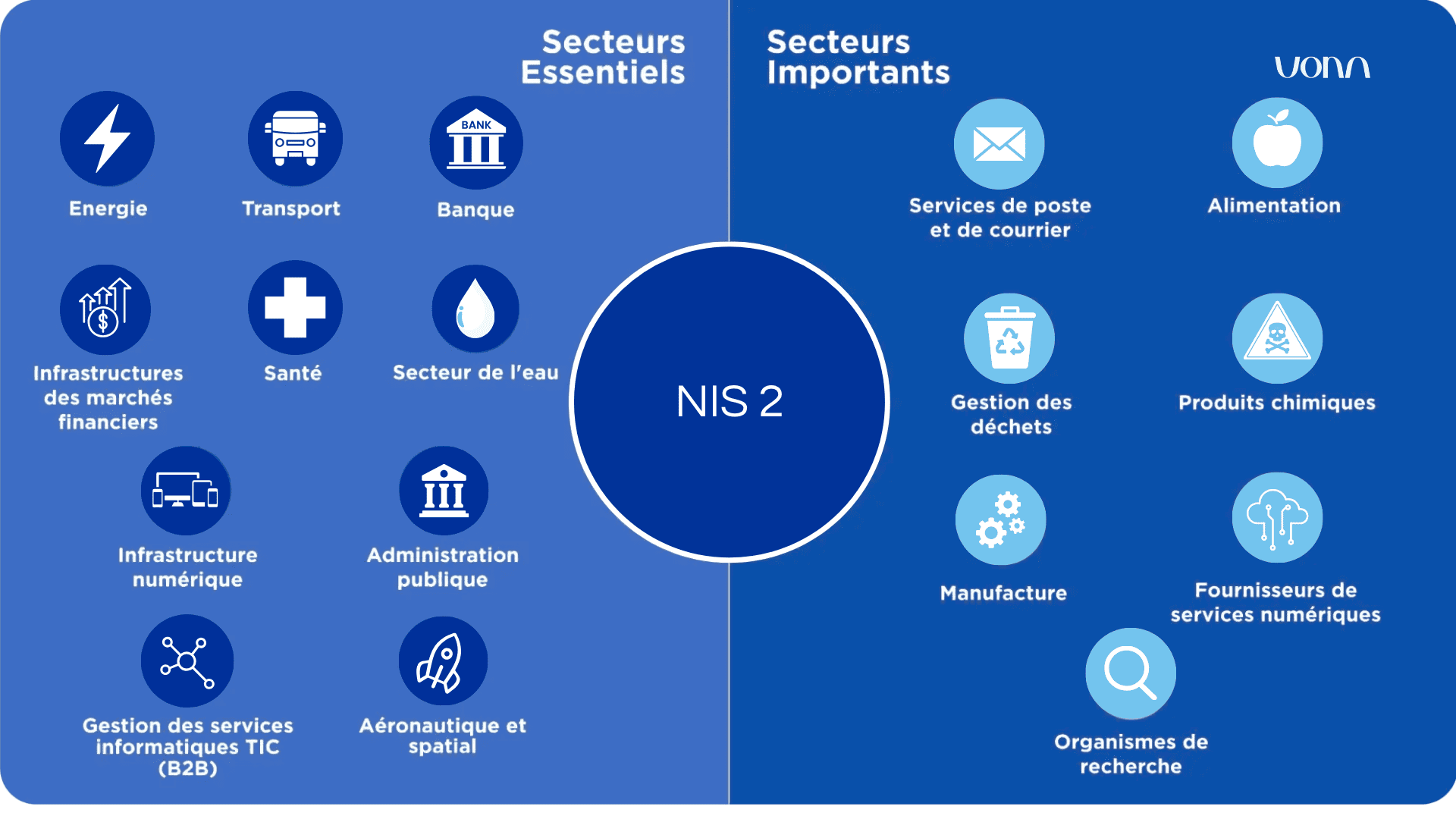
The NIS 2 directive considerably broadens its scope of application compared to NIS 1, affecting a greater number of actors and strengthening cybersecurity obligations.
It goes from 9 essential sectors for NIS 1, considered critical for the economy and society of the European Union, to 18 sectors for NIS 2.
In addition, these sectors are now classified into two categories of entities:
- Dissolution of the National Assembly: On 9 June 2024, the National Assembly was dissolved following the results of the European elections. This political situation has interrupted the examination and the vote of the bill necessary to transpose the NIS 2 Directive.
- Legislative delay: As a result, France was unable to meet the 17 October 2024 deadline for transposing the directive.
- Formal notice by the European Commission: On November 28, 2024, the European Commission officially notified 23 Member States, including France, for their delay in transposing the NIS 2 Directive.
- The “essential entities” (EE)
- the “significant entities” (EIs).
6. In detail what are these sectors concerned?
The”essential entities” include sectors critical to the functioning of society and the economy, detailed in Annex I of the NIS2 text.
The following sectors are found:
- Energy (electricity, gas, oil, district heating),
- Transport (air, rail, road, maritime),
- Banking,
- Financial market infrastructures,
- Health (including hospitals, laboratories and drug suppliers),
- Drinking water and sanitation,
- Digital infrastructures (cloud services, data centers, operators of electronic communications networks),
- Public administrations.
The”important entities” (EI), for their part, include sensitive sectors although less critical, detailed in Annex II of the NIS2 text.
This includes sectors:
- Postal and courier services,
- Industry (production of critical goods such as medical equipment, chemical products, etc.),
- Digital service providers (search engines, online platforms, social networks),
- Trusted service providers (electronic certifications, electronic signatures),
- Food sector,
- Provision of transport services (logistics, courier, delivery),
- waste management,
- Research and innovation sector (universities, research institutes),
- Armament and defense sector.
7. In practice, why is compliance essential for the entities involved?
- Strengthened cybersecurity : protection of the critical systems provided for in Article 21.
NIS 2 imposes increased measures to secure sensitive infrastructures and strengthen resilience in the face of cyber threats. - Mandatory reporting : rapid reporting of incidents provided for in Article 23.
The entities concerned must report any major incident within 24 to 72 hours and provide a final report within one month. - Strict sanctions : fines (up to 10 million euros or 2% of global annual turnover) for non-compliance and involvement of senior management of the entity
8. Strengthened cybersecurity: what does that mean in practice?
The requirements of the NIS 2 Directive, which are based on the principles established by NIS 1, present 23 safety rules divided into the following 4 areas:
- Governance: It aims to predict, monitor and continuously improve security within the organization, led by a risk committee.
- Protection: Its objective is to reduce the vulnerabilities of entities and increase the level of security of their information systems subject to the directive.
- Defense: Its purpose is to detect cybersecurity incidents and to prepare to react quickly to limit their consequences on the organization.
- Resilience : It consists in strengthening the capacity to anticipate and respond to major incidents.
9.Obligation to report cybersecurity incidents: who is it addressed to and within what timeframe?
The “essential and important entities” are required to report to ANSSI, without undue delay, any incident that has a significant impact on their services. This includes incidents:
- Causing or likely to cause a major operational interruption or financial losses for the entity concerned,
- Affecting or capable of affecting natural or legal persons by causing significant intangible, physical or moral damage.
They must also inform the users of their services without delay of incidents that may disrupt their operation. In the event of a significant cyber threat, they must communicate to the recipients concerned the corrective measures to be applied.
The ANSSI may require public communication on an incident if this makes it possible to prevent another one, to manage an ongoing incident, or if the disclosure is considered to be in the general interest.
The NIS 2 directive imposes a 3-step reporting process:
1. Initial alert: within “24 hours” after the incident was detected.
2. Detailed notification: under “72 hours”, including an update of information and a preliminary assessment.
3. Final report: to be submitted “within one month” after the initial notification, including a full assessment of the incident.
A forthcoming decree will specify the criteria for characterizing an incident as “significant” or “critical.”
Given the speed required for these NIS 2 notifications, it is mandatory for each entity to identify managers and internal procedures in order to ensure optimal responsiveness, including weekends and holidays.

10. How do you formulate a report to ANSSI?
To support the entities concerned by the NIS 2 directive, ANSSI provides a dedicated space which centralizes all useful resources: regulatory texts, guides, FAQs and procedures for reporting incidents.
The report must be made by the cybersecurity referent designated in your organization, via the ANSSI secure form.
Attention: only one person per entity (the referent) is authorized to make these reports; it is therefore not a form to be filled out every time by any employee.
But what should this report contain in practice? Here are the essential elements to fill in for an effective and compliant notification:
1. Describe the incident accurately
- Nature of the incident (ransomware attack, intrusion, data leak, etc.)
- Date and time of discovery
- Discovery circumstances (e.g. internal alert, partner notification, etc.)
- Affected systems, services, or data
2. Assess severity and impact
- Level of impact on the organization (service interruption, data loss, breach of confidentiality, etc.)
- Number of users or customers potentially affected
- Potential consequences for other actors (service providers, partners, subsidiaries...)
3. Identify the cause or threat
- Type of threat or probable cause (phishing, exploitation of a vulnerability, human error...)
- If the origin is unknown, mention it and indicate the ongoing investigations.
4. Detail the measures taken
- Actions taken to contain or resolve the incident (isolation of machines, restoration, password change, etc.)
- Measures planned in the short term to limit impacts
5. Specify the cross-border impact (if applicable)
- Possible repercussions beyond France (European subsidiaries or partners, risk of spreading to other EU entities)
6. Indicate a referring contact
- Name, function and contact details of the cybersecurity referent designated within the organization, in charge of establishing contact with ANSSI.
7. Respect the deadlines and the format
- Deadlines : Initial report within 24 hours of detection, detailed report within 72 hours, then final report once the incident is closed.
- Format : Incident reporting is done via the ANSSI secure form, reserved for the designated referent. Only one person per entity is authorized to use this form for all reports.
Structured, factual and comprehensive reporting allows ANSSI to intervene effectively and coordinate the response if necessary.
Anticipating the collection of this information and making your teams aware of the notification procedure are major assets for successful crisis management.

11. What does the concept of cybersecurity threat cover? Definition according to NIS 2
Incidents and cyber threats: a new approach under NIS 2
The NIS 2 directive abandons the criterion of”number of users affected“, used in the first version of NIS, to better structure the obligations related to incident management. It now distinguishes between two key concepts:
” The incidents ”: defined as any event that compromises the availability, authenticity, integrity or Confidentiality data or services related to networks and information systems (Article 6 (6)).
” Cyber threats ”: encompassing any potential event, action, or circumstance that may “damage, disrupt, or harm” information systems, their users, or other entities (Article 2 (8) of the Cyber Security Act, referred to in Article 6 (10) of NIS2).
According to Article 23, an incident is considered “significant” when it:
Causes or is likely to result in a” major disturbance ” services or financial losses for the entity concerned.
- Affects or could affect” other natural or legal persons ”, causing significant material or immaterial damage.
12. What are the penalties for non-compliance with NIS 2 (financial or not)? Can natural persons be involved?
The NIS 2 directive imposes strict penalties for non-compliance, with distinctions between essential entities (EE) and significant entities (EIs).
Financial sanctions:
- For essential entities (EE): fines of up to 10 million euros or 2% of global annual turnover,
- For significant entities (EIs): fines of up to 7 million euros or 1.4% of global annual turnover.
Non-financial sanctions:
- A responsibility of senior managers and C-level managers within organizations.
It is the responsibility of the CISO — but not only him — to clearly communicate to management the sanctions provided for by the NIS2 directive. In other words, this sword of Damocles should allow CISOs to get their decisions and the resulting budget increases accepted.
For information, all the sanctions and fines described above are explained in Chapter VII, Supervision and Enforcement (Articles 32, 33 and 34).

13 Our main recommendations for the correct implementation of the NIS 2 Directive
For VONA Consulting, the NIS 2 directive represents much more than a new regulatory requirement: it is a transformative opportunity for European organizations. We are convinced that compliance with NIS 2 should be considered as a strategic lever for sustainably strengthening the security of information systems and increasing resilience in the face of increasingly sophisticated digital threats.
NIS 2 is not a constraint, but a catalyst for progress. It offers businesses the opportunity to:
Effectively protect their critical infrastructures,
- Guarantee the continuity of their essential services,
- Increase the trust of their partners and customers,
- Implement proactive risk management and strengthen their operational resilience.
To support our clients in this approach, VONA Consulting recommends an integrated and structured approach, based on three major axes:
- In-depth analysis of specific obligations : We precisely identify the requirements applicable to each sector and each organization, using adapted tools (checklists, compliance maps).
- Awareness-raising and continuous training of teams : We involve all employees so that they are informed, trained and prepared to face new cybersecurity challenges.
- Preparation and effective management of crisis situations : We help implement robust protocols to anticipate, detect, and respond to incidents quickly, while ensuring business continuity.
By adopting this approach, our customers are not only meeting the requirements of NIS 2: they are strengthening their overall security posture, significantly reducing their operational risks and gaining a sustainable competitive advantage.
For VONA Consulting, NIS 2 compliance, when well thought out and managed, becomes a real driver of trust, performance and transformation in the service of the future.
Useful links:
Directive (EU) 2022/2555 of the European Parliament and of the Council of 14 December 2022 on measures for a high common level of cybersecurity across the Union, amending Regulation (EU) No 910/2014 and Directive (EU) 2018/1972, and repealing Directive (EU) 2018/1972, and repealing Directive (EU) 2016/1972, and repealing Directive (EU) 2016/1148 (NIS 2 Directive) (Text with EEA relevance)
https://cyber.gouv.fr/sites/default/files/2022-12/formulaire-declaration-incident-lpm_anssi.pdf
https://monespacenis2.cyber.gouv.fr/simulateur




.png)
.png)